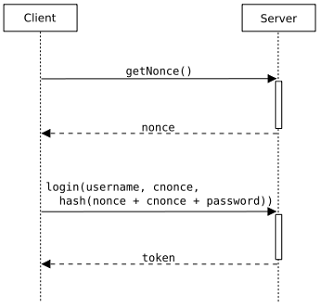
This Two-Way Cryptograph was the continuation of one-way cyptograph implementation, and more simple than the previous one. This type of cryptography may often referred to as cryptographic "real", because it has the "encrypt" to transform plain text into cipher text, and the "decrypt" to restore cipher text into plain text. In this type of cryptography, in addition to plain text and cipher text, it takes another parameter called "key". Currently there are two types of keys are used, the "Symmetric Key" and "Assymetric Key".
The thing to remember in this process is a two-way cryptography, encrypt and decrypt process should have a conflicting operation. For example, the encrypt process we use the operator "+" (plus), then decrypt the process we have to use the operator "-" (minus). Therefore, the implementation of the encrypt and decrypt kriptografinya made into two different implementations, but complementary. To decrypt processes, implementation will emulate a software serial verification process, while the process encrypt, implementation will act as a "keygen" it.
skip to main |
skip to sidebar
Cryptograph Implementation Part 2 (Two-Way Cryptograph)
Advertisement
Labels:
Computer World,
Programming Languages,
Tips Komputer,
Tutorial
Advertisement
Related Posts : Cryptograph Implementation Part 2 (Two-Way Cryptograph)
Advertisement
Popular Post
- Cara Meningkatkan Traffic Blog (FULL)
- Microsoft Office 2007 Product Key Free
- Microsoft Surface : the new Generation of multi touch Computer
- Trik SEO pada Postingan Blog, Menyamarkan Tag
- Get Free Access Internet WiFi
- Jenis dan Macam Backlink
- Cara hack hotspot mikrotik
- Free Download Modul Belajar Microsoft Office Access
- Trik Mengubah Windows XP menjadi genuine
- 4shared premium download generator
Get Free Updates
Android
(7)
Blogging
(28)
Computer Networking
(11)
Computer World
(67)
Download
(6)
Games
(9)
Google
(10)
Hacking
(18)
iPhone Tips
(2)
Lain - lain
(30)
Linux OS
(9)
Mac OS
(1)
Mobile Phone
(12)
Network
(8)
News
(92)
Online Bussiness
(34)
Optimization Problems
(48)
Programming Languages
(8)
Security
(8)
Social Networking
(48)
Software
(9)
Technology
(59)
Tips Blog
(42)
Tips Internet
(128)
Tips Komputer
(155)
Tips Ms. Office
(9)
Trik SEO blogspot
(15)
Tutorial
(38)
Tutorials
(48)
Virus
(2)
Windows OS
(75)
Translate My Page
Recent Comments
All Contents Copyright © 2014 KartoloCyber

0 comments:
Post a Comment